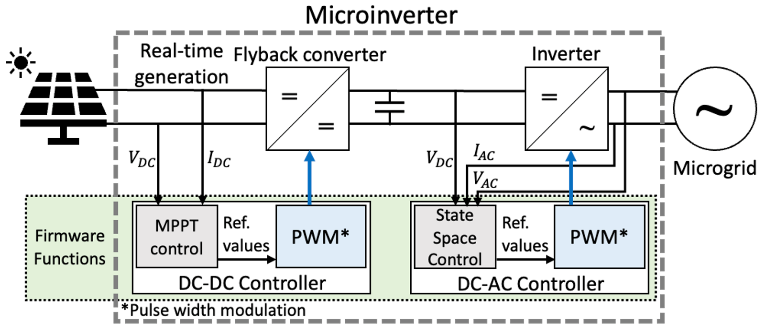
Firmware Attacks on Micro-Inverter Controllers
Along with the plethora of advantages furnished by inverter-based resources (IBR) and distributed generation (DG), some disadvantages should be factored in when performing cybersecurity analyses. Specifically, many embedded controllers responsible for orchestrating the operation of IBR are resource-constrained and/or were not developed with security in mind. Firmware modifications represent a class of attacks that aims to modify the control logic within embedded systems and deteriorate their performance. By carefully crafting such attacks through firmware functions (Figure 1), critical inverter firmware functions can be compromised, e.g., MPPT capability, their switching and output stages driving logic, introducing uneconomical operation, voltage and frequency instabilities, power quality degradations or even jeopardizing the underlying assets by exceeding their nominal operational limits.
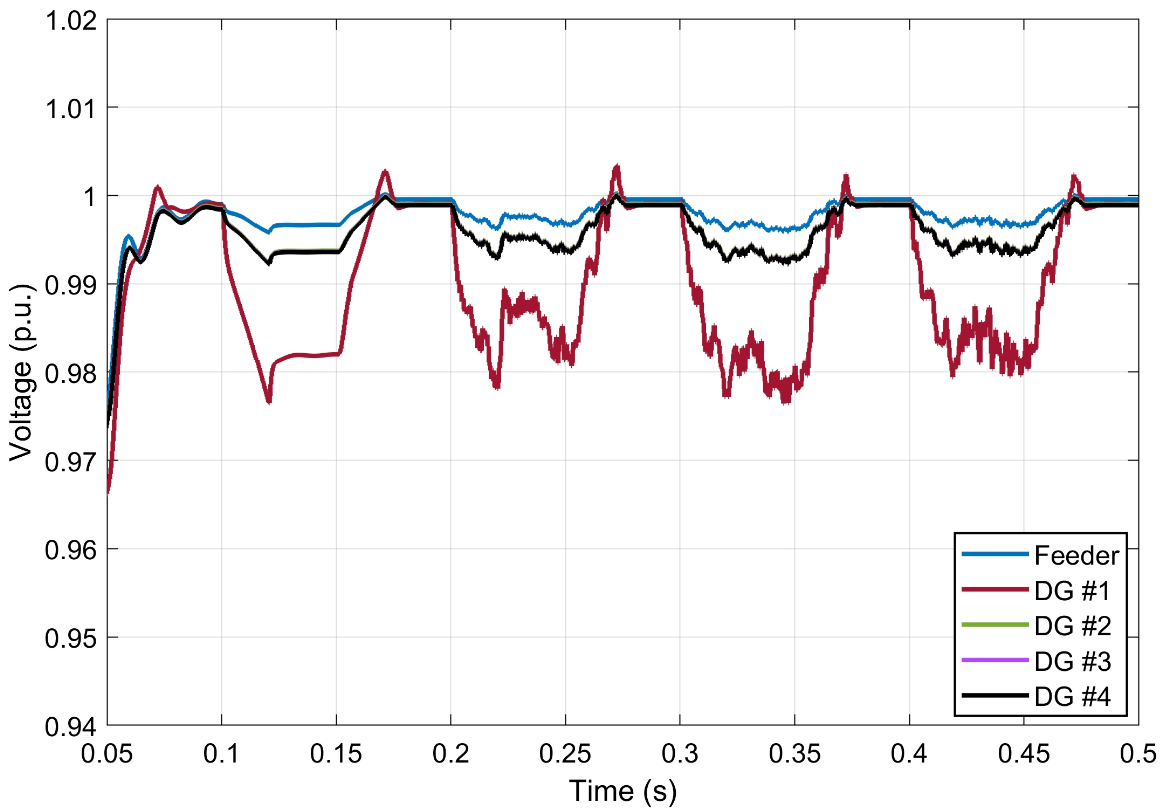
In Figure 2, we demonstrate the impact of combined switching (disabling the inverter’s output stage) and additive (inserting perturbations on the control signals) attacks on an IBR resource. For these simulations, we have used a modified version of the Canadian urban distribution feeder, which has been adapted to include inverter-based DG. We can also observe that the firmware attacks targeting the inverter of DG #1 have a propagating effect on the neighbouring DG nodes (Figure 2). To effectively detect such firmware-level compromises, we leverage hardware performance counters (HPCs).
HPCs are special circuits embedded within the central processing unit of electronic devices and monitor specific events, for instance, how many times a particular command has been performed, the function has been called, etc.
Using HPCs, we can detect patterns that indicate the execution of malicious functions on our devices with minimum performance and redesign overheads. Specifically, we have demonstrated that malicious firmware in inverter controllers can be detected with 97.22% accuracy using a single HPC that meets our original objective for a low-cost and low-complexity defense countermeasure.
I. Zografopoulos, A. P. Kuruvila, K. Basu, C. Konstantinou, "Time series-based detection and impact analysis of firmware attacks in microgrids", Energy reports, vol. 8, pp. 11221-11234,
2022. DOI: https://doi.org/10.1016/j.egyr.2022.08.270